In July, we covered Pegasus Spyware and Zero-Click Attacks. Pegasus was developed by the NSO Group and sold to governments for the official purpose of spying on criminals and terrorists. According to the Pegasus Project, some of NSO Group’s clients used it to spy on civilian political dissidents, including journalists, activists, and government officials. Zero-click attacks were used to install Pegasus onto victim smartphones, and from there, Pegasus would spy on everything: calls, texts, GPS locations, etc. A zero-click attack is what it sounds like: an attack that works without requiring victims to click on anything, unlike a phishing attack, which typically requires the user to click on something. This week, the Citizen Lab, based out of the University of Toronto, released a new report related to Pegasus, titled FORCEDENTRY: NSO Group iMessage Zero-Click Exploit Captured in the Wild. This report documents the discovery of a zero-click exploit used for Pegasus. While re-analyzing the iTunes backup of the phone of a targeted activist, the researchers discovered 27 identical copies of a file with a “.gif” extension that were actually copies of an Adobe PSD (Photoshop) file, and four different “.gif” files that were really Adobe PDF files. When the Photoshop files were processed as GIFs, they would cause IMTranscoderAgent—a part of the iMessage processing pipeline—to crash. The zero-click exploit, named FORCEDENTRY, was designated as CVE-2021-30860 by Apple. According to the description of CVE-2021-30860, the vulnerability is exploited by “processing a maliciously crafted PDF”, which “may lead to arbitrary code execution.” The Citizen Lab notes that the actual vulnerability itself is “an integer overflow vulnerability in Apple’s image rendering library (CoreGraphics).” The Common Weakness Enumeration (CWE) succinctly explains what an integer overflow, or wraparound, is:
An integer overflow or wraparound occurs when an integer value is incremented to a value that is too large to store in the associated representation. When this occurs, the value may wrap to become a very small or negative number. While this may be intended behavior in circumstances that rely on wrapping, it can have security consequences if the wrap is unexpected. This is especially the case if the integer overflow can be triggered using user-supplied inputs. This becomes security-critical when the result is used to control looping, make a security decision, or determine the offset or size in behaviors such as memory allocation, copying, concatenation, etc.
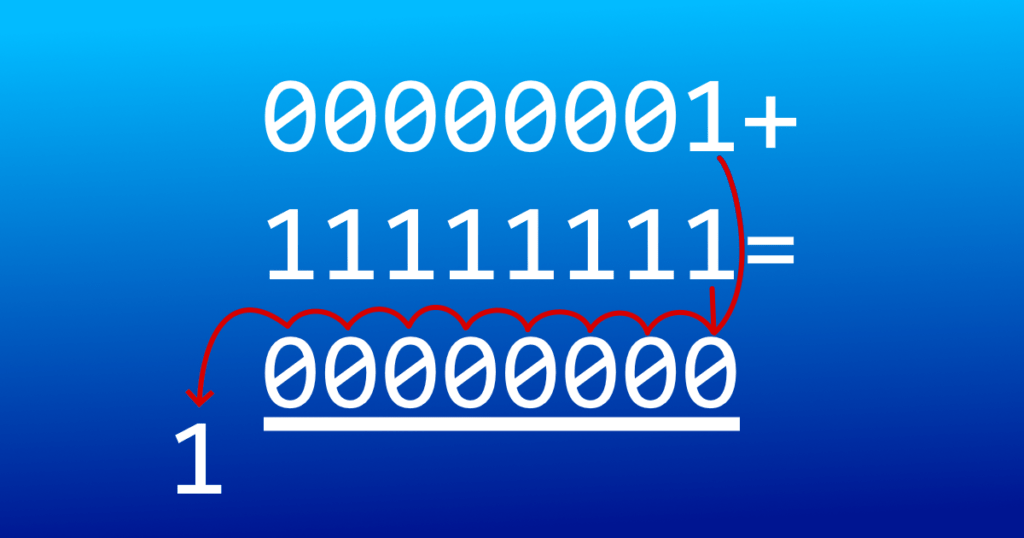
To provide a more elaborate explanation, computers store numbers in binary form, binary digits are called bits, and each bit is either a 1 or a 0. Integers are represented via sequences of bits. The binary equivalent of 0 is “0”, and the binary equivalent of 1 is “1”, but 2 is represented as “10”, 3 is “11”, 4 is “100”, 5 is “101”, 6 is “110”, 7 is “111”, 8 is “1000”, etc. The range of possible values is determined by the number of bits representing the integer. For example, 8-bit unsigned integers—integers which are either zero or positive—have 2^8, or 256 possible values. These include 0, so the range is from 0 to 255. What happens if you try to add 1 to an 8-bit integer that is 255, or “11111111” in binary? The last “1” would get carried over to the leftmost position, but since the 9-bit long binary equivalent of 256, or “100000000”, cannot be stored as an 8-bit integer, you would be left with “00000000”, or 0. With signed integers—integers that can be zero, positive, or negative—the leftmost bit, or sign bit, represents the sign: 0 for positive or zero, 1 for negative. For signed integers, overflows happen when two large integers with the same sign are added together, but the sign bit gets flipped during the addition, so the result would have the opposite sign. If a program expects the result of arithmetic to be positive but gets a negative result instead (or vice-versa), it could act in unexpected ways, such as starting an infinite loop that leads to a crash.
In our previous blog post, we explained what a buffer overflow vulnerability is. Buffer overflows and integer overflows are similar in that they can be caused by improper input validation and can have serious consequences for application security. Both kinds of vulnerabilities can be prevented when programmers are cautious about how the underlying logic of applications handles inputs. Fortunately for Apple device owners, Apple fixed the integer overflow vulnerability in security updates for iOS 14.8 and iPadOS 14.8, watchOS 7.6.2, macOS Big Sur 11.6, and macOS Catalina. If you own Apple devices with these operating systems prior to these versions, installing the latest updates would be a good idea.
If you are curious about the details of how addition and subtraction are typically performed for signed integers, look up Two’s Complement. Thomas Finley of Cornell University provided a good explanation.